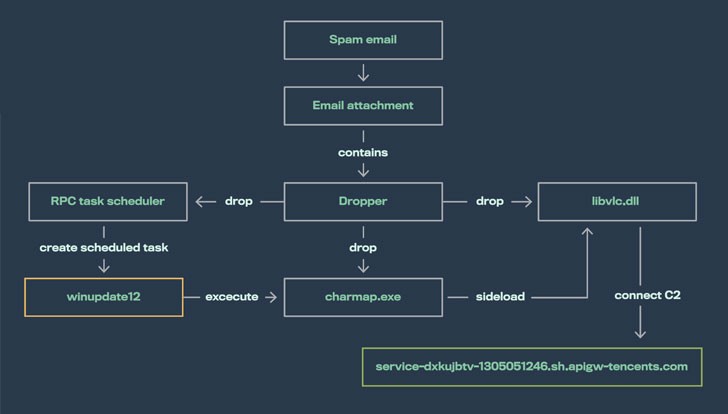
In recent years, Chinese and Russian hackers have turned to increasingly sophisticated methods to evade detection. One such example is the use of SILKLOADER malware, which enables them to load Cobalt Strike onto infected machines.
As cybersecurity companies continue to improve their detection capabilities, cybercriminals must constantly adapt and find new ways to propagate their tools. This article explores the emergence of SILKLOADER, its ties to Chinese and Russian hackers, and the broader implications for cybersecurity.
The Emergence of SILKLOADER Malware
Finnish cybersecurity company WithSecure has discovered a new malware, dubbed SILKLOADER, that is being used by threat actors affiliated with Chinese and Russian cybercriminal ecosystems. This malware leverages DLL side-loading techniques to deliver commercial adversary simulation software, specifically the Cobalt Strike framework.
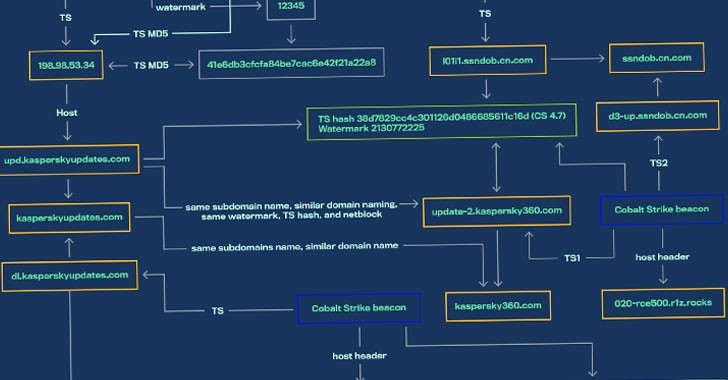
This development has come as a response to improved detection capabilities against Cobalt Strike, a legitimate post-exploitation tool used for red team operations.
SILKLOADER and Its Kin: KoboldLoader, MagnetLoader, and LithiumLoader
SILKLOADER is not the only loader used by cybercriminals to incorporate Cobalt Strike components. Other recently discovered loaders include KoboldLoader, MagnetLoader, and LithiumLoader. Both SILKLOADER and LithiumLoader employ DLL side-loading methods to hijack legitimate applications with the goal of running a separate, malicious dynamic link library (DLL).
SILKLOADER in Action: A Closer Look at Recent Attacks
WithSecure has identified the use of SILKLOADER in several human-operated intrusions targeting a wide range of organizations in Brazil, France, and Taiwan in the last quarter of 2022. While these attacks were ultimately unsuccessful, they are suspected to be a precursor to ransomware deployments. In one instance, a French social welfare organization was targeted, and the threat actor gained a foothold in their network by exploiting a compromised Fortinet SSL VPN appliance to stage Cobalt Strike beacons.

The Packer-as-a-Service Model: SILKLOADER’s Role in the Cybercriminal Ecosystem
SILKLOADER is believed to be offered as an off-the-shelf loader through a Packer-as-a-Service program to Russian-based threat actors. This means that the loader is provided either directly to ransomware groups or via groups offering Cobalt Strike and Infrastructure-as-a-Service to trusted affiliates. WithSecure’s analysis suggests that most of these affiliates have had close working relationships with the Conti group, its members, and offspring after its alleged shutdown.
The Origins and Evolution of SILKLOADER
SILKLOADER samples analyzed by WithSecure reveal that early versions of the malware date back to the beginning of 2022. Initially, the loader was exclusively used in attacks targeting victims in China and Hong Kong. The shift from East Asian targets to countries like Brazil and France is believed to have occurred around July 2022. Since then, all SILKLOADER-related incidents have been attributed to Russian cybercriminal actors.
This suggests that SILKLOADER was initially developed by threat actors within the Chinese cybercriminal ecosystem and was later acquired by a Russian threat actor. This acquisition is believed to have occurred between July 2022 and September 2022, when the original Chinese author sold the loader to a Russian threat actor after it was no longer of use to them.
⭐️⭐️⭐️⭐️⭐️ Best Antivirus for 2023
Avast Ultimate 2023 | 10 Device 2 Years | Antivirus+Cleaner+VPN+AntiTrack, [PC/Mac/Android] [Digital Code]
Avast Ultimate 2023 | 10 Device 2 Years | Antivirus+Cleaner+VPN+AntiTrack | [PC/Mac/Android] [Digital Code]
Avast Ultimate 2023 is an all-in-one bundle that provides protection, privacy, and performance enhancements for Windows, Mac, Android, and iOS devices. This digital code ensures fast delivery and installation, with real-time antivirus and anti-hacker protection, PC webcam security, and premium mobile anti-theft features.
Full Features:- Real-time antivirus and anti-hacker protection
- PC webcam security
- Premium mobile anti-theft
- Private browsing, banking, and online shopping
- Disguise your location to browse without restrictions
- Boost device speed and battery life
- Remove junk data, duplicate files, and unwanted photos
Warranty & Service: The license key and official download link will be sent to your email within 24 hours after purchase. No physical product is shipped.
Other Users Opinion: Users appreciate the comprehensive protection offered by Avast Ultimate 2023 and the convenience of receiving the digital code quickly via email.
Pros:
- Comprehensive protection for multiple devices
- Quick digital delivery
- Enhanced privacy features
- Improved device performance
Cons:
- No physical product available
Upgrading from the free Avast One Essential for Mac to Avast One for Mac eliminates VPN restrictions and adds useful features such as blocking browser fingerprints, monitoring breaches for your data, and freeing up disk space. The antivirus protection is highly rated by AV-Test Institute and AV-Comparatives, and the user interface is attractive and easy to use.
Full Features:- Antivirus protection with excellent lab results
- Ransomware protection
- Web Shield for safe browsing
- Email Guardian protection
- Network Inspector feature
- Compatible with macOS 10.13 (High Sierra) or higher
Warranty & Service: Avast One for Mac is a digital product with no physical shipping. The license key and download link will be sent to your email within 24 hours of purchase.
Other Users Opinion: Mac users are pleased with the added features and enhanced security provided by upgrading to Avast One for Mac.
Pros:
- Excellent antivirus protection
- Comprehensive security features
- Attractive user interface
- Quick digital delivery
Cons:
- Requires macOS 10.13 (High Sierra) or higher
Both Avast Ultimate 2023 and Avast One for Mac offer comprehensive protection, privacy, and performance enhancements for your devices. Users appreciate the convenience of quick digital delivery and the peace of mind provided by these highly rated security solutions. Upgrading to the paid versions of these products unlocks additional features and offers a more robust security experience.
Recommended reading: The Best Bitcoin and Ethereum Hardware Wallets for 2023
The Implications of SILKLOADER and BAILLOADER for Cybersecurity
SILKLOADER and BAILLOADER are prime examples of how threat actors continually refine and retool their approaches to stay ahead of the detection curve. As the cybercriminal ecosystem becomes more modularized through service offerings, it is increasingly difficult to attribute attacks to specific threat groups based solely on the components used in their attacks.
The Growing Threat of Ransomware and Malware-as-a-Service
The rise of SILKLOADER and BAILLOADER highlights the growing threat of ransomware and malware-as-a-service offerings. These services enable cybercriminals to access sophisticated tools and techniques, allowing them to carry out more effective and damaging attacks. As a result, organizations must invest in robust cybersecurity measures and adopt a proactive approach to protect their networks and data.

The Importance of Collaboration and Information Sharing
To counter the evolving threat landscape, it is essential for cybersecurity companies, researchers, and law enforcement agencies to collaborate and share information. By pooling resources and knowledge, these organizations can develop a more comprehensive understanding of emerging threats, such as SILKLOADER, and work together to develop strategies to combat them.
Staying Ahead of the Cybercriminal Curve
As cybercriminals continue to innovate and adapt to new technologies and detection methods, it is crucial for organizations to remain vigilant and prioritize cybersecurity. This includes regular security audits, employee training, and the adoption of advanced security solutions.
Conclusion
In conclusion, the rise of SILKLOADER malware demonstrates the ongoing evolution of cybercriminal tactics and the increasing sophistication of their tools. As these threats continue to grow, organizations must recognize the importance of staying ahead of the curve by investing in strong cybersecurity measures and fostering collaboration among industry stakeholders. By doing so, they can better protect themselves from the ever-evolving landscape of cyber threats.





![Avast Ultimate 2023 | 10 Device 2 Years | Antivirus+Cleaner+VPN+AntiTrack, [PC/Mac/Android] [Digital Code]](https://m.media-amazon.com/images/I/413xz0SCwTL.jpg)


